产品信息
Software Vulnerabilities Notice Regarding Evident Microscope Software
Due to a severe security vulnerability issue in a third-party component used in Evident Application Software, it is strongly advised to install the provided Service Update. This Service Update provides a version of the affected component that closes the vulnerability gap.
The target software is as follows.
- cellSens
Entry, Standard, Dimension, Dimension Desktop, APEX Version 3.2 or later (launched 2021) - VS120
VS-ASW, VS-Desktop, DB Admin, NIS / SQL Version 2.9.2 or later (launched 2019) - VS200
VS200-ASW, VS200-Desktop, DB Admin, NIS / SQL Version 3.1 or later (launched 2019) - OLYMPUS Stream
Current: Stream Enterprise, Stream Enterprise Desktop, SFR
Legacy: Stream Start, Stream Basic, Stream Essentials, Stream Motion, Stream Desktop)
Version 2.4 or later (launched 2019) - CIX
CIX-ASW, CIX-SZX Version 1.4 or later (launched 2019) - PRECiV
Capture, Core, Pro, Desktop, DSX Version 1.1 or later (launched 2022) - DP2-AOU Version 1.1 or later (launched 2020)
As a result of our survey, it revealed that there are two vulnerabilities.
CVE-2023-3935: A heap buffer overflow vulnerability in Wibu CodeMeter Runtime
CVE-2023-38545: This flaw makes curl overflow a heap based buffer in the SOCKS5 proxy handshake
Please see for more information.
Product Security Advisory WIBU-230704-01-v3.0
https://cdn.wibu.com/fileadmin/wibu_downloads/security_advisories/AdvisoryWIBU-230704-01-v3.0.pdf
Product Security Advisory WIBU-231017-01
https://cdn.wibu.com/fileadmin/wibu_downloads/security_advisories/AdvisoryWIBU-231017-01.pdf
NIST(*1) NVD(*2)
https://nvd.nist.gov/vuln/detail/CVE-2023-3935
https://nvd.nist.gov/vuln/detail/CVE-2023-38545
(*1) NIST: National Institute of Standards and Technology
(*2) NVD: National Vulnerability Database
The impact of the security vulnerability
CVE-2023-3935
The impact depends on where CodeMter is installed.
a) CodeMeter Runtime (i.e., CodeMeter.exe) is configured as a server
Successful exploitation of this vulnerability could allow an unauthenticated remote attacker to execute code on vulnerable products.
b) CodeMeter Runtime is configured as a client
An authenticated local attacker to gain root/admin privileges on vulnerable products.
CVE-2023-38545
Customer floating license server and listed applications above use the affected CodeMeter Runtime which internally use the libcurl in a version that is vulnerable to a buffer overflow attack if curl is configured to redirect traffic through a SOCKS5 proxy.
A malicious proxy can exploit a bug in the implemented handshake to cause a buffer overflow.
If you have installed the CodeMeter license server yourself, sending manipulated packets can cause a crash of it or possibly code can be smuggled in and executed.
Workaround
Install the provided Service Update.
If auto update function is enabled, it appears the notice to install service update on your PC.
(For DP2-AOU users)
Please refer to the "Installing dedicated device drivers" section of the instruction manual and prepare to apply the update.
Furthermore, if you have enabled DP2-AVS (Antivirus software license), please also refer to "Preparing to launch the installation/update program" section of the instruction manual.
This service update is available for the following operating systems.
- Windows 10 (32-bit / 64-bit)
- Windows 8 / 8.1 (32-bit / 64-bit)
- Windows 11 (64-bit)
- Windows Server 2012 (64-bit)
- Windows Server 2016 (64-bit)
- Windows Server 2019 (64-bit)
- Windows Server 2022 (64-bit)
Confirmation before installation
Make sure that all applications are closed.
Installation Procedure
1. Start Windows.
2. Log on with administrator rights.
3. Download the Service Update file (CodeMeter_7_60d.exe) from the below.
https://serviceupdates.olympus-sis.com/DownloadArea
4. Make sure that all applications are closed.
5. Double-click the Service Update file.
6. If the user account control dialog is displayed, select 'Yes'.
7. When you are asked if you want to install CodeMeter 7.60d confirm with ‘Yes’.
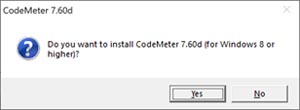
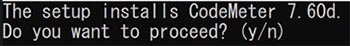
8. A console window appears, type ‘y’ to confirm and proceed.
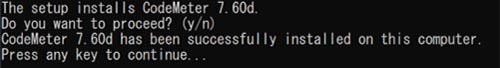
9. When the setup is complete, press any key to close the console window.
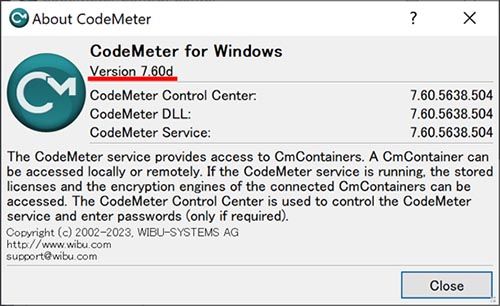
10. Check the version of CodeMeter.
Right-click from the CodeMeter tool on the task bar and click ‘About’ to verify that it is version 7.60d.
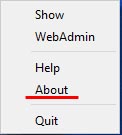
(For DP2-AOU users)
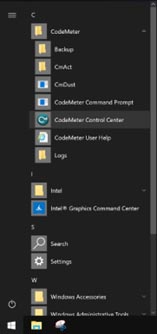
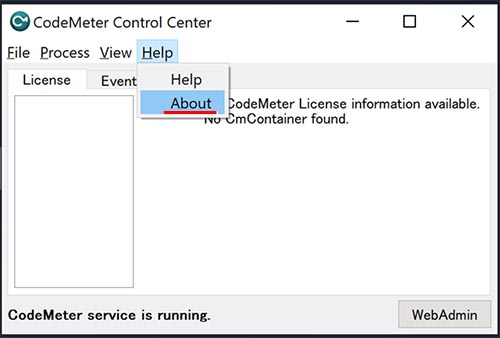
Launch "CodeMeter Control Center" from the Windows menu, then select "About CodeMeter Control Center" from the menu of the application and verify that it is version 7.60d.
If you are using the cellSens or Stream, and have enabled the auto update function, please take the following actions.
1. If you are connected to the internet, it appears the update notice dialog on your PC when you start the software.
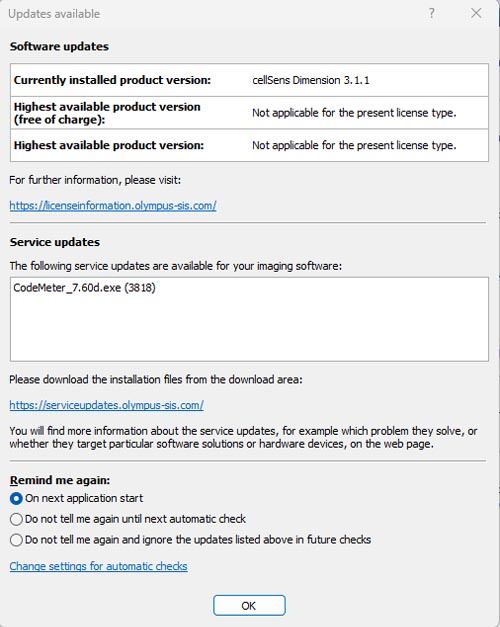
Select ‘Do not tell me again and ignore the updates listed above in future checks’ on Update notice dialog, then press ‘OK’.
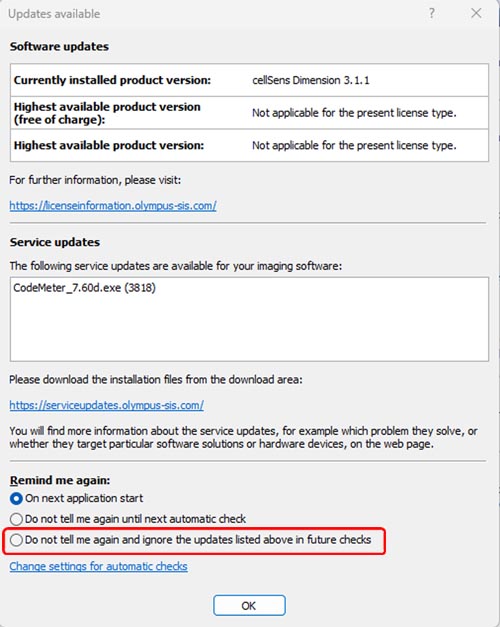
2. If it appears the update notice dialog on your PC before updates, check the version of CodeMeter.
(a) The case that the version of CodeMeter is 7.60d.
Select ‘Do not tell me again and ignore the updates listed above in future checks’ on reminder dialog, then press ‘OK’.
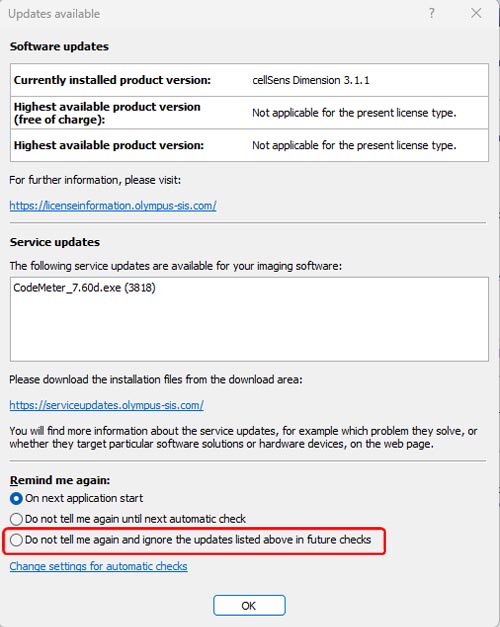
(b) The case that the version of CodeMeter is NOT 7.60d.
Install the Service Update according to the above installation procedure.
对不起,此内容在您的国家不适用。